July 19, 2017
Category:
AWS
IAM role which allows specific user to view EC2 instance without the permission to launch
You already know how to create a policy from IAM Policies Part 2 of our tutorials.Keep in mind to use naming convention which can help you in the feature use.
You can follow the steps below to create a custom policy which allow a user only to view EC instance but does not allow the same user to lunch a new one.
- From Identity Access Management console choose Policies and then Create Policy.
- Choose Create Your Own Policies
- Policy name pattern is in the following format: ec2-vpc-role-poc, my advice is to include a short description.
- It is important to enter ACCOUNTNUMBER, REGION and VPC-ID correctly.
- ACCOUNTNUMBER is 5555555555555
- REGION is eu-central-1
- VPC-ID is vpc-09ac3161
{ "Version": "2012-10-17", "Statement": [ { "Sid": "NonResourceBasedReadOnlyPermissions", "Action": [ "ec2:Describe*", "ec2:CreateKeyPair", "ec2:CreateSecurityGroup", "iam:GetInstanceProfiles", "iam:ListInstanceProfiles" ], "Effect": "Allow", "Resource": "*" }, { "Sid": "IAMPassRoleToInstance", "Action": [ "iam:PassRole" ], "Effect": "Allow", "Resource": "arn:aws:iam::<strong>555555555555</strong>:role/<strong>role-vpc-restriction-test</strong>" }, { "Sid": "AllowInstanceActions", "Effect": "Allow", "Action": [ "ec2:RebootInstances", "ec2:StopInstances", "ec2:TerminateInstances", "ec2:StartInstances", "ec2:AttachVolume", "ec2:DetachVolume" ], "Resource": "arn:aws:ec2:<strong>eu-central-1</strong>:<strong>555555555555</strong>:instance/*", "Condition": { "StringEquals": { "ec2:InstanceProfile": "arn:aws:iam::<strong>555555555555</strong>:instance-profile/<strong>role-vpc-restriction-test</strong>" } } }, { "Sid": "EC2RunInstances", "Effect": "Allow", "Action": "ec2:RunInstances", "Resource": "arn:aws:ec2:<strong>eu-central-1:55555555555</strong>5:instance/*", "Condition": { "StringEquals": { "ec2:InstanceProfile": "arn:aws:iam::<strong>555555555555</strong>:instance-profile/<strong>role-vpc-restriction-test</strong>" } } }, { "Sid": "EC2RunInstancesSubnet", "Effect": "Allow", "Action": "ec2:RunInstances", "Resource": "arn:aws:ec2:<strong>eu-central-1:555555555555</strong>:subnet/*", "Condition": { "StringEquals": { "ec2:vpc": "arn:aws:ec2:<strong>eu-central-1:555555555555</strong>:vpc/<strong>vpc-09ac3161</strong>" } } }, { "Sid": "RemainingRunInstancePermissions", "Effect": "Allow", "Action": "ec2:RunInstances", "Resource": [ "arn:aws:ec2:<strong>eu-central-1:555555555555</strong>:volume/*", "arn:aws:ec2:<strong>eu-central-</strong>1::image/*", "arn:aws:ec2:<strong>eu-central-1</strong>::snapshot/*", "arn:aws:ec2:<strong>eu-central-1:555555555555</strong>:network-interface/*", "arn:aws:ec2:<strong>eu-central-1:555555555555</strong>:key-pair/*", "arn:aws:ec2:<strong>eu-central-1:555555555555</strong>:security-group/*" ] }, { "Sid": "EC2VpcNonresourceSpecificActions", "Effect": "Allow", "Action": [ "ec2:DeleteNetworkAcl", "ec2:DeleteNetworkAclEntry", "ec2:DeleteRoute", "ec2:DeleteRouteTable", "ec2:AuthorizeSecurityGroupEgress", "ec2:AuthorizeSecurityGroupIngress", "ec2:RevokeSecurityGroupEgress", "ec2:RevokeSecurityGroupIngress", "ec2:DeleteSecurityGroup" ], "Resource": "*", "Condition": { "StringEquals": { "ec2:vpc": "arn:aws:ec2:<strong>eu-central-1:555555555555</strong>:vpc/<strong>vpc-09ac3161</strong>" } } } ] }
Attach the policy to a user, group or role
- From IAM console navigation pane, choose Users (the steps are similar for Groups and Roles).
- Choose Policy type and then Customer Managed Policies
- Choose the policy created above and then choose Attach Policy.
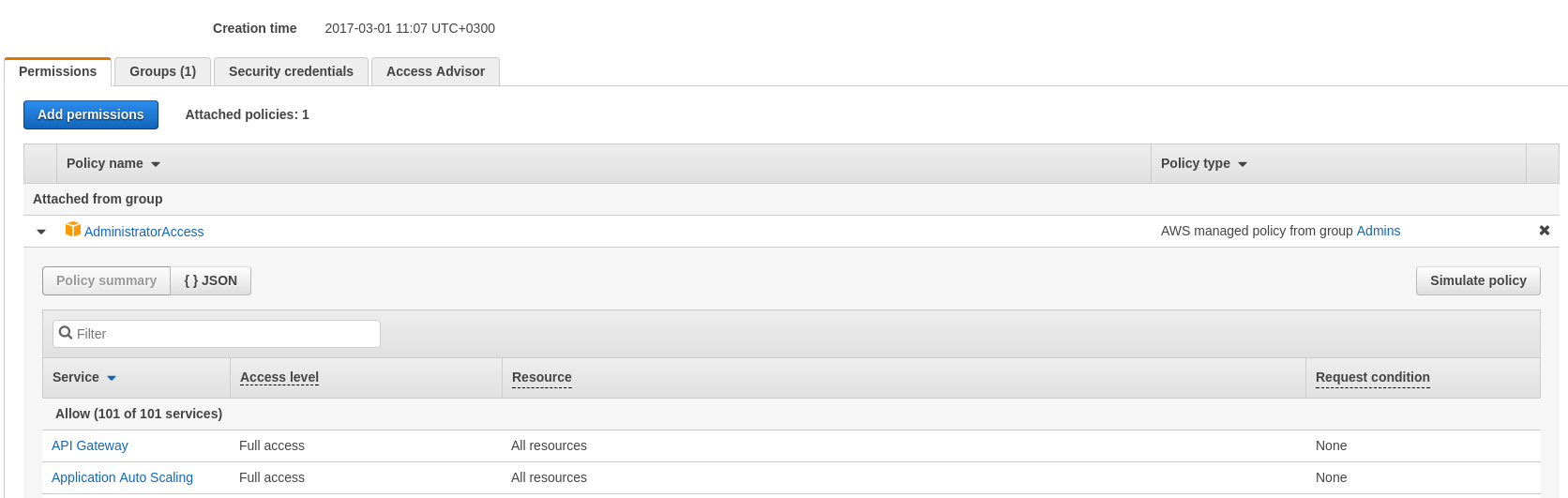
You can do this for different services and different options for each. Refer to AWS documentation Common Scenarios for role examples.